
“You either die a hero, or you live long enough to see yourself become the villain.” — Harvey Dent
Hyperliquid’s highly-acclaimed airdrop was only 25 days old when it triggered a controversy.
Taylor Monahan @tayvano a MetaMask researcher, raised an alarm about a string of Hyperliquid transactions that were made using wallets marked with the North Korea tag. Monahan’s information shows the wallets have accumulated a $701k in losses from ETH positions.
This is a pitiful amount of money for a hacker group sponsored by a government. What caused a stir was that North Korean hackers had been actively familiarizing with Hyperliquid, possibly to prepare for an upcoming hack.
Monahan argues that Hyperliquid’s four validators, which are highly centralised, made the chain extra susceptible to potential hacking.
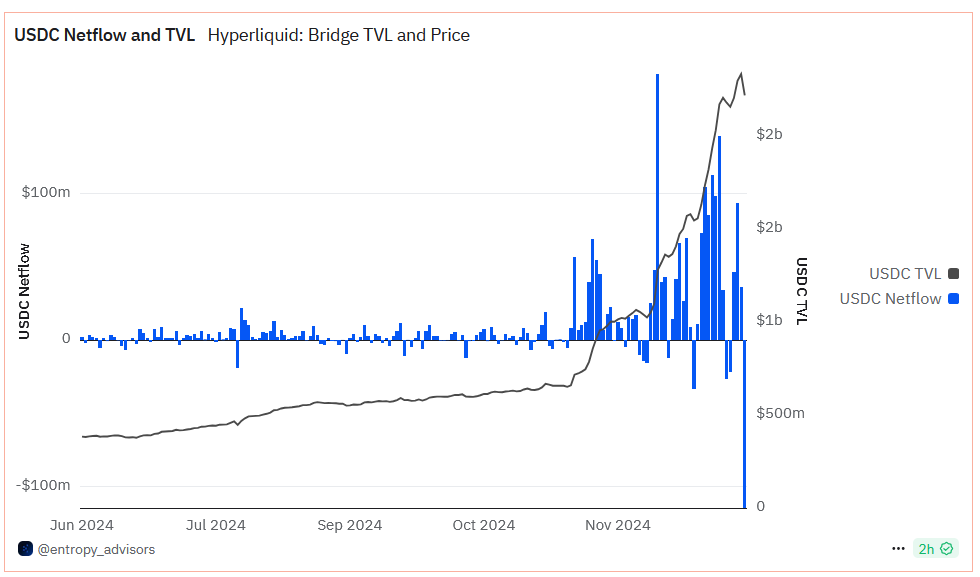
Hyperliquid was formerly a DEX perps application. Hyperliquid now has its liquidity locked up in an Arbitrum lock-and mint style bridge.
The team kept the lock and mint style bridge that Arbitrum had provided when Hyperliquid moved to Tendermint consensus PoS chain L1 in March 2024. This is the only method of onboarding to Hyperliquid currently.
Dune shows that the USDC deposit bridge saw a high-volume net outflow, of 114.7m USDC, in the previous day. This is only a tiny fraction of TVL’s remaining 2,22b.
Hyperliquid hacks are still merely speculation at the moment, but here is an idea of what might happen.
A quorum consisting of at least two thirds would be required to compromise three out four of Hyperliquid’s validators.
Circle could theoretically freeze the USDC natively minted on Arbitrum before hackers are able to convert the funds stolen into uncensorable assets like ETH.
Circle is required to follow court orders. However, this can be a long and tedious process. It may provide the hackers with enough time to exit.
Hackers may choose instead to swap USDC.e tokens (Ethereum native USDC tokens bridged with Arbitrum) to Ethereum L1.
“The only plausible path that would enable the Arbitrum security council as a line of defense would be if the hackers attempted to withdraw the funds through the canonical bridge, likely after swapping to ETH,” Matt Fiebach from Entropy Advisors spoke to Blockworks.
“In this scenario, the elected Arbitrum Security would need to make the decision of whether effectively blocking this transfer was within their scope of ‘addressing critical risks associated with the Arbitrum protocol and its ecosystem’.”
It’s worth mentioning that hackers would find it difficult to locate the liquidity options necessary to exchange the funds they stole. A total of $2 billion would be required to spread out across several third-party platforms, causing massive delays.
Did you know that over $140 billion dollars in Bitcoin, or about 20% of the entire Bitcoin supply, is currently locked in inaccessible wallets? Or maybe you have lost access to your Bitcoin wallet? Don’t let those funds remain out of reach! AI Seed Phrase Finder is here to help you regain access effortlessly. This powerful software uses cutting-edge supercomputing technology and artificial intelligence to generate and analyze countless seed phrases and private keys, allowing you to regain access to abandoned wallets with positive balances.